Yes, or use flakes which gives you a lockfile pinning everything. But this is related to reproducibility, not immutability.
- 0 Posts
- 13 Comments
I’ve had NixOS absolutely refuse to run some compiler toolchain I depended upon that should’ve been dead simple on other distros, I’m really hesitant to try anything that tries to be too different anymore.
Yes, some toolchain expect you to run pre-compiled dynamically linked binaries. These won’t work on NixOS, you need to either find a way to install the binary from nix and force the toolchain to use it or run
patchelfon it somehow.
Well that was an approximation to keep it simple and disprove the given example. There are other directories in the root filesystem that are in the path by default, or used in some other critical way (like
/etc). Even if they are links to directories in the nix store you can replace the link.
These seems to be related to flatpak, not immutability.
To be honest I don’t know these very well. I only use NixOS. My understanding is that in an immutable distribution the root filesystem is read-only. Granted in NixOS the nix store is immutable and most things in the root filesystem are just links to the nix store, but the root filesystem itself is not read-only.
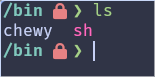
I’m on NixOS right now and just dropped a Chewy in my
/bin, only had tosudo touch /bin/chewy.
if it’s being read from, it can be written to.
Why would being able to read imply being able to write?
Having an extra step or two in the way doesn’t make it “extremely secure”.
Well it can greatly improve security by preventing a compromised app to achieve persistence.
The store is immutable but the system itself definitely isn’t.
I don’t know, if your goal is security Pixels have the best hardware and GrapheneOS the best software. It makes a lot of sense.
Being decentralized prevents DNS or IP blocks but not blocks through DPI.
Signal has an option to masquerade it’s traffic as regular HTTPS, I don’t know if Matrix can do such a thing.



Isn’t immutability related to the root filesystem being read-only? I can write on my root filesystem, even if it’s mostly links to the store I can replace those links.